Firebase Functions Config Best Practice – How to store private keys in Firebase Functions
This guide demonstrates the best practices for storing private keys in Firebase Functions config. Currently, there are two methods available: v1 and v2.
Storing Secret Keys in Firebase Function v1
In Firebase Function v1, it was recommended to add private keys through runtime environment configuration using the Firebase CLI. Please refer to this link for more information on firebase functions config.
Storing Secret Keys in Firebase Function v2
Firebase Function v2 introduced parameterized configuration, which is now recommended for most cases. Follow the steps below to store secret keys:
Adding Keys via Firebase CLI
To set the key, navigate to the functions folder and execute the following command:
Firebase functions:secrets:set [KEY_NAME]
Here is an example:
MacBook-Pro functions % firebase functions:secrets:set TEST_KEY
? Enter a value for TEST_KEY [hidden]
✔ Created a new secret version projects/*********/secrets/TEST_KEY/versions/1
MacBook-Pro functions %
To check the version and state of the key, run the following command within the functions folder:
Firebase functions:secrets:get [KEY_NAME]
Here is an example:
MacBook-Pro functions % firebase functions:secrets:get TEST_KEY
┌─────────┬─────────┐
│ Version │ State │
├─────────┼─────────┤
│ 1 │ ENABLED │
└─────────┴─────────┘
MacBook-Pro functions % To delete the key, use the command:
Firebase functions:secrets:destroy [KEY_NAME]
Here is an example:
MacBook-Pro functions % firebase functions:secrets:destroy TEST_KEY
? Are you sure you want to destroy TEST_KEY@1 Yes
i Destroyed secret version TEST_KEY@1
i No active secret versions left. Destroying secret TEST_KEY
erickim@Erics-MacBook-Pro functions % Adding Keys directly in Google Cloud Secret Manager
To add a key directly in Google Cloud Secret Manager, follow these steps:
Go to the Google Cloud Secret Manager
Click on “Console” located in the middle of the page.
Ensure that you have selected the appropriate project by using the dropdown menu in the upper left corner.
*** If you are working on multiple projects, it is important to select the project you are currently working on to access the key from your Firebase Functions project. Otherwise, the key will be in a different folder.
Click “+ CREATE SECRET” to add your private key.
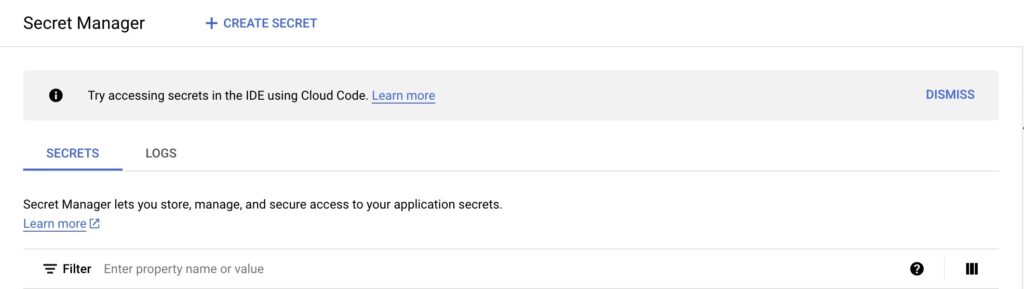
Fill out the necessary details to add a new key, including the name, secret value (either by uploading a file or copying and pasting the key directly), rotation settings, and label.
Click “Create.”
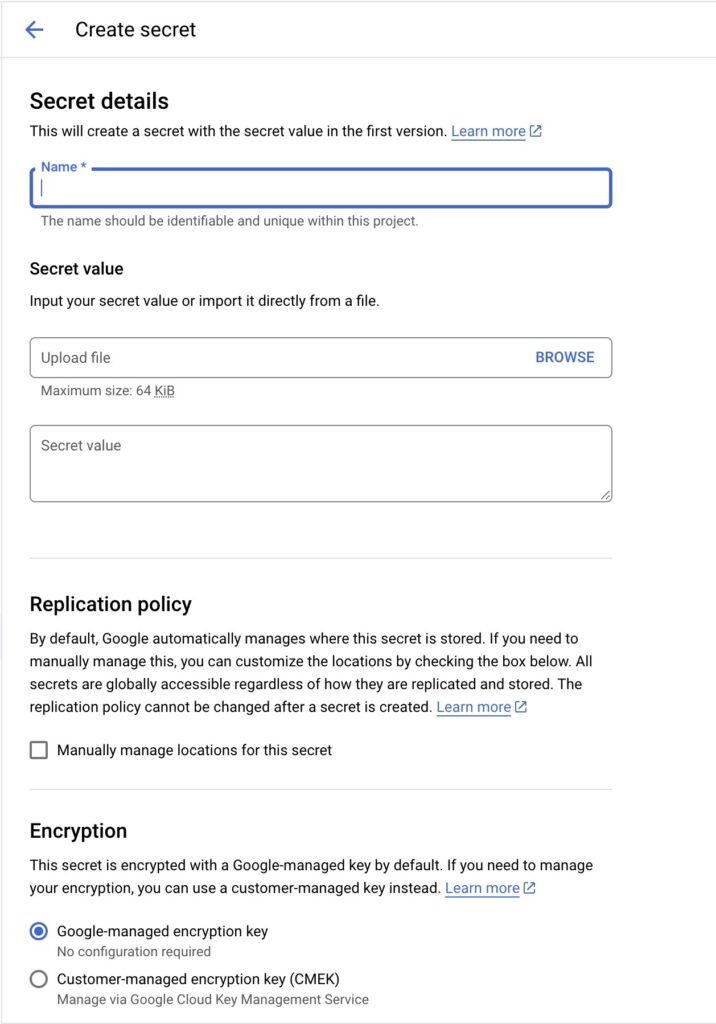
Once created, you will see the key listed as shown below.
To test if you have access to the key, use the following command within your project:
Firebase functions:secrets:get [KEY_NAME]
Accessing Keys in Firebase Functions with Node.js
Please note that this guide is for Firebase Functions v2.
First, need to create a variable and assign/import “firebase-functions/params”
Secondly, need to declare a variable and pass in the name of the key
Lastly, you can access the key by calling the variable defined with .value().
Please refer to the code example below.
const { onRequest } = require("firebase-functions/v2/https");
const { defineSecret } = require("firebase-functions/params");
const sgMail = require('@sendgrid/mail');
const testkey = defineSecret("TEST_KEY");
exports.testAPI = onRequest({ secrets: [testkey] }, async (req, res) => {
// How to set the key
sgMail.setApiKey(testkey.value());
});Join our community of mobile app enthusiasts and stay ahead of the curve. Sign up for our newsletter today!






Leave a Reply